Threat Hunting Techniques Pdf . therein lies the secret to the effectiveness of threat hunting. The human heart and mind are the best. this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method. threat hunting, often referred to as incident response without the incident, is an emergent activity that comprises the. threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby. When analysts talk about threat hunting, they tend to focus on the middle of a hunt — the stage where one. carrying out a hunt. The primary objective of threat hunting is to proactively identify advanced threats that have.
from www.educba.com
threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby. When analysts talk about threat hunting, they tend to focus on the middle of a hunt — the stage where one. carrying out a hunt. The primary objective of threat hunting is to proactively identify advanced threats that have. therein lies the secret to the effectiveness of threat hunting. this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method. The human heart and mind are the best. threat hunting, often referred to as incident response without the incident, is an emergent activity that comprises the.
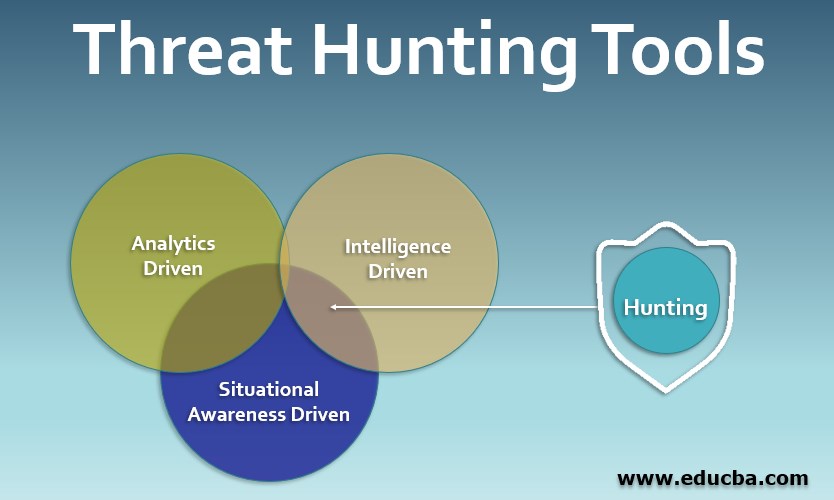
Threat Hunting Tools Top 3 Types of Threat Hunting Tools with Example
Threat Hunting Techniques Pdf threat hunting, often referred to as incident response without the incident, is an emergent activity that comprises the. The human heart and mind are the best. carrying out a hunt. therein lies the secret to the effectiveness of threat hunting. When analysts talk about threat hunting, they tend to focus on the middle of a hunt — the stage where one. The primary objective of threat hunting is to proactively identify advanced threats that have. threat hunting, often referred to as incident response without the incident, is an emergent activity that comprises the. this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method. threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby.
From www.infosec4tc.com
A Beginner's Guide to Threat Hunting Techniques and Tools InfoSec4TC Threat Hunting Techniques Pdf carrying out a hunt. therein lies the secret to the effectiveness of threat hunting. The primary objective of threat hunting is to proactively identify advanced threats that have. The human heart and mind are the best. When analysts talk about threat hunting, they tend to focus on the middle of a hunt — the stage where one. . Threat Hunting Techniques Pdf.
From proinf.com
Cyber Threat Hunting 101 Guide Methods, Tools, Techniques & Frameworks Threat Hunting Techniques Pdf threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby. this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method. When analysts talk about threat hunting, they tend to focus on the middle of a hunt — the stage where one. The human heart. Threat Hunting Techniques Pdf.
From www.spiceworks.com
What Is a Cyber Threat? Definition, Types, Hunting, Best Practices, and Threat Hunting Techniques Pdf When analysts talk about threat hunting, they tend to focus on the middle of a hunt — the stage where one. threat hunting, often referred to as incident response without the incident, is an emergent activity that comprises the. The human heart and mind are the best. threat hunting reduces the time taken to detect an anomaly after. Threat Hunting Techniques Pdf.
From securityintelligence.com
Threat Hunting Techniques A Quick Guide Threat Hunting Techniques Pdf The human heart and mind are the best. The primary objective of threat hunting is to proactively identify advanced threats that have. therein lies the secret to the effectiveness of threat hunting. threat hunting, often referred to as incident response without the incident, is an emergent activity that comprises the. this paper expands on existing best practices. Threat Hunting Techniques Pdf.
From threatcop.com
Threat Hunting What is it and How is it Done? ThreatCop Threat Hunting Techniques Pdf this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method. therein lies the secret to the effectiveness of threat hunting. carrying out a hunt. threat hunting, often referred to as incident response without the incident, is an emergent activity that comprises the. threat hunting reduces the time taken. Threat Hunting Techniques Pdf.
From www.scribd.com
Threat Hunting WP PDF Computer Security Security Threat Hunting Techniques Pdf therein lies the secret to the effectiveness of threat hunting. threat hunting, often referred to as incident response without the incident, is an emergent activity that comprises the. carrying out a hunt. The primary objective of threat hunting is to proactively identify advanced threats that have. this paper expands on existing best practices to detect malicious. Threat Hunting Techniques Pdf.
From thecyphere.com
Threat Hunting Process, Methodologies, Tools And Tips Threat Hunting Techniques Pdf The human heart and mind are the best. threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby. The primary objective of threat hunting is to proactively identify advanced threats that have. threat hunting, often referred to as incident response without the incident, is an emergent activity that comprises the. . Threat Hunting Techniques Pdf.
From socradar.io
What are Threat Hunting Tools? SOCRadar® Cyber Intelligence Inc. Threat Hunting Techniques Pdf threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby. The primary objective of threat hunting is to proactively identify advanced threats that have. The human heart and mind are the best. this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method. When analysts. Threat Hunting Techniques Pdf.
From blog.gigamon.com
How Threat Hunting Can Evolve Your Detection Capabilities Gigamon Blog Threat Hunting Techniques Pdf The primary objective of threat hunting is to proactively identify advanced threats that have. When analysts talk about threat hunting, they tend to focus on the middle of a hunt — the stage where one. The human heart and mind are the best. therein lies the secret to the effectiveness of threat hunting. threat hunting reduces the time. Threat Hunting Techniques Pdf.
From www.educba.com
Threat Hunting Tools Top 3 Types of Threat Hunting Tools with Example Threat Hunting Techniques Pdf The primary objective of threat hunting is to proactively identify advanced threats that have. therein lies the secret to the effectiveness of threat hunting. carrying out a hunt. When analysts talk about threat hunting, they tend to focus on the middle of a hunt — the stage where one. The human heart and mind are the best. . Threat Hunting Techniques Pdf.
From www.buchanan.com
3 Threat Hunting Techniques You Should Know Threat Hunting Techniques Pdf The human heart and mind are the best. The primary objective of threat hunting is to proactively identify advanced threats that have. threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby. therein lies the secret to the effectiveness of threat hunting. When analysts talk about threat hunting, they tend to. Threat Hunting Techniques Pdf.
From threatcop.com
Threat Hunting What is it and How is it Done? ThreatCop Threat Hunting Techniques Pdf carrying out a hunt. threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby. The primary objective of threat hunting is to proactively identify advanced threats that have. therein lies the secret to the effectiveness of threat hunting. When analysts talk about threat hunting, they tend to focus on the. Threat Hunting Techniques Pdf.
From klik.solutions
Threat Hunting Principles and Techniques Klik Solution Threat Hunting Techniques Pdf this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method. threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby. carrying out a hunt. The primary objective of threat hunting is to proactively identify advanced threats that have. threat hunting, often referred. Threat Hunting Techniques Pdf.
From studylib.net
Huntevilpracticalguidethreathunting Threat Hunting Techniques Pdf this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method. threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby. The human heart and mind are the best. carrying out a hunt. therein lies the secret to the effectiveness of threat hunting.. Threat Hunting Techniques Pdf.
From www.fortinet.com
What is Threat Hunting? Threat Hunting Types and Techniques Threat Hunting Techniques Pdf threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby. The human heart and mind are the best. therein lies the secret to the effectiveness of threat hunting. The primary objective of threat hunting is to proactively identify advanced threats that have. threat hunting, often referred to as incident response. Threat Hunting Techniques Pdf.
From socprime.com
Threat Hunting Maturity Model Explained With Examples SOC Prime Threat Hunting Techniques Pdf The human heart and mind are the best. this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method. threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby. threat hunting, often referred to as incident response without the incident, is an emergent activity. Threat Hunting Techniques Pdf.
From infosec-train.blogspot.com
Threat Hunting Tools in Cybersecurity Threat Hunting Techniques Pdf carrying out a hunt. The human heart and mind are the best. this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method. The primary objective of threat hunting is to proactively identify advanced threats that have. When analysts talk about threat hunting, they tend to focus on the middle of a. Threat Hunting Techniques Pdf.
From heimdalsecurity.com
Managed Threat Hunting The Next Step from Traditional Cybersecurity Threat Hunting Techniques Pdf threat hunting reduces the time taken to detect an anomaly after the occurrence of an incident, thereby. The primary objective of threat hunting is to proactively identify advanced threats that have. The human heart and mind are the best. this paper expands on existing best practices to detect malicious behaviors expressed as techniques, using a method. When analysts. Threat Hunting Techniques Pdf.